Secure Access Service Edge (SASE)
All about what SASE (Secure Access Service Edge) is and how it can be the solution for your IT security in the cloud.
We are witnessing the most significant transformation since industrialization. As a result, extremely much IT is being placed in the cloud. We have for a long period been accustomed to sending all sorts of solutions into the cloud. Still, if one had suggested to one’s CISO five years ago that the security components should run from the cloud, one would hardly have been taken seriously.
Where are we today?
Not everything – but many IT security solutions are either managed or running from the cloud. Futurists, such as Gartner, expect this development to continue, and solutions such as SASE should be delivered as a service from the cloud.
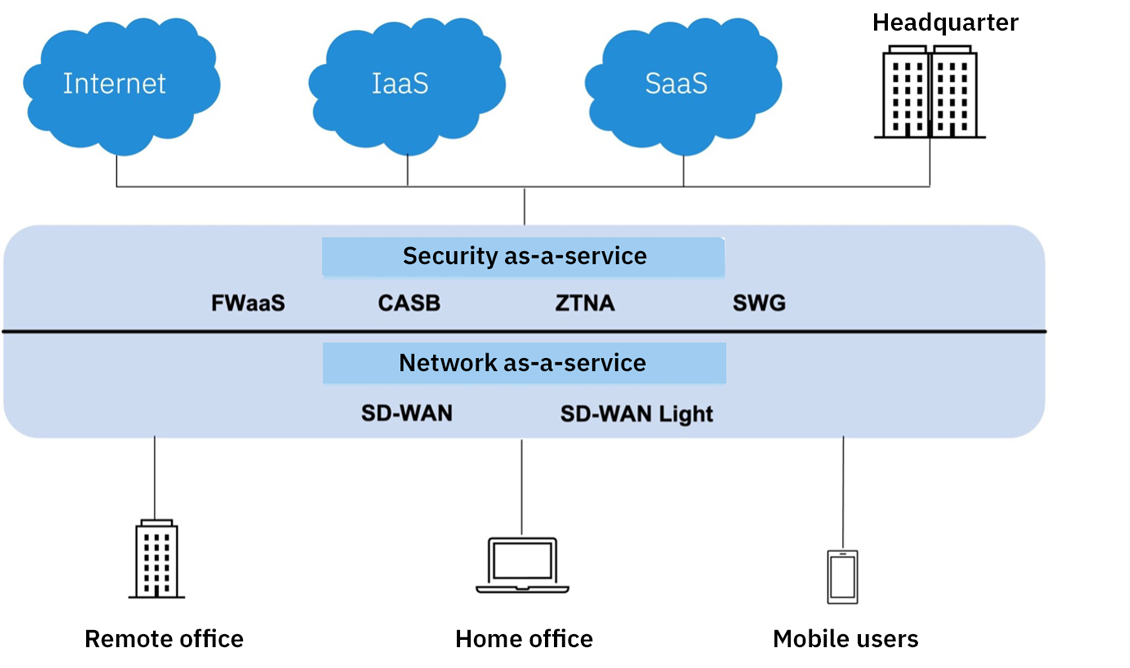
Figure text: Sase – simplified description
When did SASE enter the scene?
Gartner defined SASE (Secure Access Service Edge) in 2019, and SASE currently peaks in Gartner’s Hype Cycle. Gartner divides SASE into three functions:
- core
- recommended
- optional
Manufacturers typically support all features or parts of them. However, as a potential SASE buyer, you must be aware that some Manufacturers are bending the definition of SASE so that their particular solution can be marketed as SASE.
What is SASE – Secure Access Service Edge?
The SASE Architecture consists of a combination of network, security, and identity. I have tried to illustrate the components below.
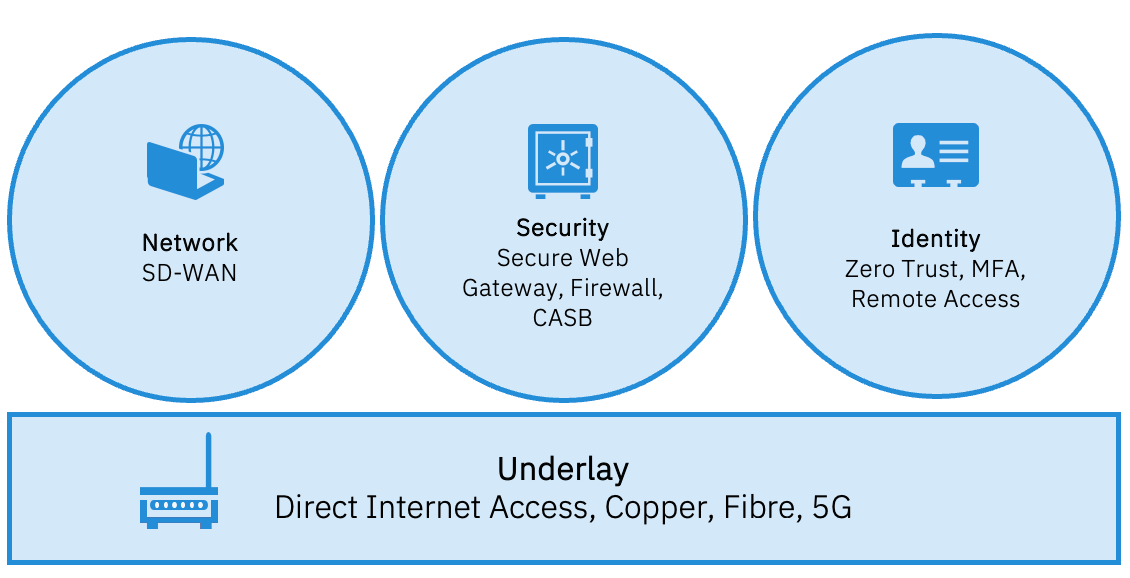
Simply put, a SASE solution without the security components is not SASE, and likewise, there is no SASE without SD-WAN because the concepts are related.
The Corona Pandemic has accelerated the SASE hype. Although we are probably on the other side of the pandemic, users are still located very fragmented, working at home, in the office, in a cafe, or somewhere else.
SaaS applications have contributed significantly to us being able to function professionally under COVID, where the cloud became our data center. Therefore, the need for DIA (direct internet access) has become the new normal to ensure a good user experience.
There is a question that needs to be asked, though:
“How do we stand concerning IT security when IT security becomes decentralized and a cloud thing?”
SASE may be one of the answers.
SASE reduces complexity and costs
As a starting point, you as a company should choose a complete solution from one supplier. This will reduce the number of hardware and software agents versions and thus contribute to a more straightforward “operations” setup.
With a central management tool, corporate security teams can define policies that are distributed and enforced close to end-users.
End-users should have the same experience, no matter what resources they need and where they access them. Therefore, the user experience depends on how distributed the individual SASE provider is (i.e., how many POPs and SASE gateways they have). The SD-WAN solution must, of course, be able to be integrated with these gateways. If you are a company with a global presence, this is a part that you should include in your evaluation of SASE (PoC / PoV).
As mentioned in the introduction, SASE introduces cloud-based security. FWaaS, CASB, ZTNA, and SWG are the four core technologies. In addition to these, both recommended and optional technologies exist in Gartner’s definitions. One of these is DNS security, which in my opinion, is very valuable.
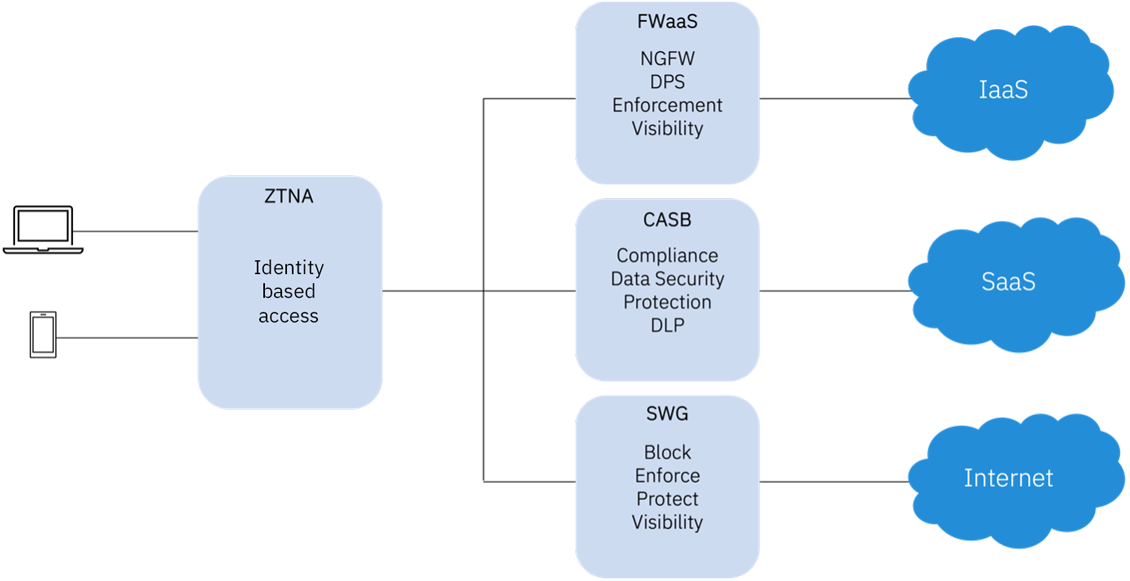
SASE simplifies the access process by tagging relevant security policies for the resources the user is trying to access based on the user’s login. It enhances security by enforcing security policies wherever the user is located.
SASE is based on Zero-Trust access (ZTNA), so access is based on user-level instead of IP address.
How to get started? As for all IT projects, a good place to start is to identify the needs of the company or business unit. An example could be to find out if the need is a full SD-WAN solution or if you as a company can be “satisfied” but a slightly lighter version such as Cisco Meraki.
The next step could be an assessment and transformation plan. Then, get an overview of which security solutions you have on-prem, which could make sense to move in the cloud, and within what time frame.
Make a supplier PoC / PoV. Here you often find out which solution is best for the company. In addition, one becomes wiser about which parts of SASE add value if they are ‘turned on.’
Competencies, competencies, competencies
Build competencies. It can not be said often enough. If you as a company want to utilize the security solutions that exist in the cloud, it is essential that you have competencies that can proactively and reactively understand and utilize them. However, for some companies, it can be difficult and costly to build a sufficient level of competence in-house. Many companies can lean on a Managed Service Partner and get outside help in these cases.
NIL (part of Conscia Group) has partnerships with Cisco, Palo-Alto, and VMware, who are all serious about their SASE portfolio, and we are therefore in a good position to guide our customers. If you need an in-depth dialogue, you are welcome to contact us.
Author: Henrik Møll, CTO, Conscia Denmark
Cloud security with Cisco Secure Access Service Edge (SASE)
Watch the lecture by Stojan Rančić from NIL and learn how to provide pervasive user, data and application security by leveraging the Cisco SASE approach.
