Cyber-Threat Protection for Decentralized Networks
Your employees work remotely and in the office. Your organization uses both on-premises, as well as cloud services and applications. Consequently, a lot of work is done over the internet, out of the corporate network you can control.
As the network traffic moves out of the perimeter, it gets more vulnerable to cybercriminals and internet threats. So, how can you protect your traffic and communications over networks that are not under your control?

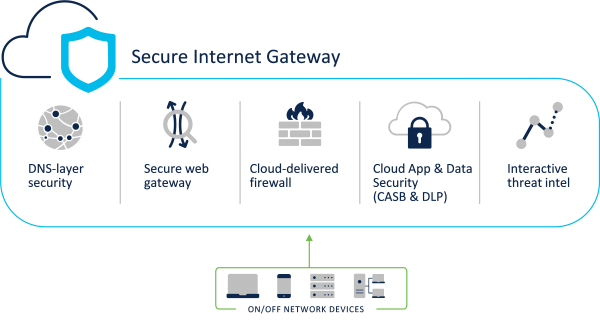
NIL’s Managed Secure Internet Gateway (SIG) brings together secure web gateway, DNS-layer security, cloud-delivered firewall, cloud access security broker functionality, and threat intelligence within a single solution. It protects your data and applications across decentralized networks.
The solution is delivered from the cloud and is easy to deploy, so it also significantly reduces the effort usually needed to set up such a level of network security control.
Firewall, Web Gateway, Threat Intelligence, and Cloud Access Security Broker Combined in a Single Solution
The Managed Secure Internet Gateway solution secures internet access and controls cloud app usage from your network, branch offices, and roaming users. The solution acts as a secure on-ramp to the internet and delivers deep inspection and control to support compliance and provide effective threat protection.
The solution’s key features include:
- DNS-layer security: Blocking the high-risk domains associated with phishing, malware, botnets, and other malicious activity, as well as customer-provided domains communicated via the enforcement API. With appropriate solution licensing, direct-to-IP C2 Callback traffic can also be detected and filtered.
- Secure Web Gateway: Web traffic filtering (domain, category or URL-based), including custom block/allow lists. Detailed web traffic analysis including SSL traffic decryption and inspection and advanced malware detection with the cloud sandbox analysis.
- Cloud-delivered firewall: Layer 3 – Layer 7 cloud-delivered firewall with IPsec Tunnel termination.
- Cloud access security broker: Shadow IT discovery and blocking, using domains and URLs with optional granular controls for posts, and attachments and uploads blocking within selected applications.
- Threat intelligence investigation: Web-console based threat intelligence investigation, enhanced by an on-demand enrichment API allowing Domain, URL, IP, and File threat intelligence inputs from 3rd parties.
- Traffic forwarding: External DNS traffic forwarding for on-premise (Meraki MR, ISR, WLC, Aerohive, Cradlepoint) and off-premise (Cisco AnyConnect, Umbrella Roaming client, CSC for iOS) protection and network traffic aggregation via PAC files, proxy chaining and IPsec tunnels.
- User Identity integration: Policy and report creation based on internal subnets, network devices, egress IP addresses, roaming devices, AD group membership, and SAML.
- Solution management: Web-dashboard or API-based solution control, including the creation of custom block pages and bypass options.
- Reporting and logging: Region-specific (North America, EU) log storage with manual and API-based real-time and historical activity search across DNS, URL, and Firewall logs.
The Managed Secure Internet Gateway solution is based on Cisco Umbrella technology.
Managed Secure Internet Gateway Components
The Managed Secure Internet Gateway solution comprises multiple components which align with the solution licensing model. Different components allow using the solution in different ways – from providing lightweight DNS-based access control for roaming users, routing all customer traffic via an IPsec tunnel to a full-fledged Layer-7 cloud-based firewall.
The solution’s key components are:
- DNS-layer security: This is the first line of defense against threats because DNS resolution is the first step in internet access. Enforcing security at the DNS and IP layers, SIG blocks requests to malicious and unwanted destinations before a connection is even established — stopping threats over any port or protocol before they reach your network or endpoints. As a cloud-delivered service, it:
- Provides the visibility needed to protect internet access across all network devices, office locations, and roaming users.
- Logs and categorizes DNS activity by the type of security threat or web content and the action taken — whether it was blocked or allowed.
- Retains logs of all activity for as long as needed, ready to recall for deeper investigation.
- Can be implemented quickly to cover thousands of locations and users in minutes to provide immediate return on investment.
-
Advanced components, such as Cloud-delivered Firewall and Cloud Access Security Broker.
- Secure web gateway (SIG): The SIG solution includes a cloud-based full proxy that can log and inspect all of your web traffic for greater transparency, control, and protection. That includes:
-
The ability to efficiently scan all uploaded and downloaded files for malware and other threats using the Cisco AMP engine and third-party resources.
- Full or selective SSL decryption to further protect your organization from hidden attacks and time-consuming infections.
-
Granular application controls to block specific user activities in select apps (e.g. file uploads to Dropbox, attachments to Gmail, posts/shares on Facebook).
- File type blocking (e.g. block download of .exe files).
-
Detailed reporting with full URL addresses, network identity, allow or block actions, plus the external IP address.
-
Content filtering by category or specific URLs to block destinations that violate policies or compliance regulations.
-
- Correlated threat intelligence for improved incident response: The SIG solution analyzes over 200 billion DNS requests daily. It ingests a massive amount of internet activity data from a global network and continuously runs statistical and machine learning models against it. The unique view of the internet enables Cisco to uncover malicious domains, IPs, and URLs before they are used in attacks. The security researchers constantly analyze this information and supplement it with intelligence from Cisco Talos to discover and block an extensive range of threats.
Solution Architecture
More Information
To learn more about Managed Secure Internet Gateway solution and how it can secure your business, contact our team.